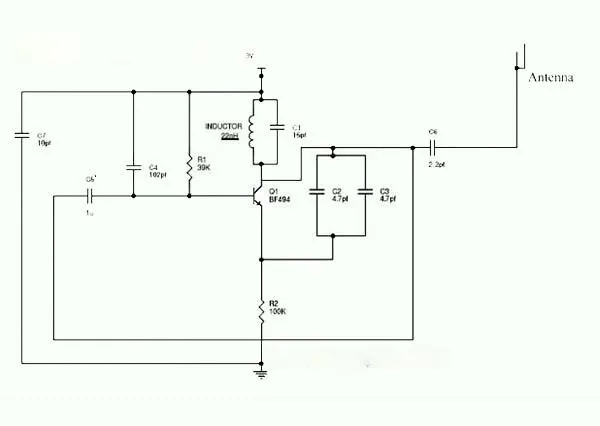
At present, there are many kinds of signal locator cell phone jammer and mobile phone communication jammers sold and used on the market, and their working principles are basically the method of white noise multi-band scanning and wide frequency spectrum coverage. The power of the interference signal emitted is far It is greater than the power of the communication signal transmitted by the base station to achieve the purpose of blocking the communication channel between the base station and the mobile terminal.

The mobile phone monitoring and intelligent management and control system developed is a device that can perform MSIIMEI code detection, communication control, and mobile phone number acquisition on mobile phones of all three major operators based on mobile communication technology in specific areas and specific environments.
At the same time, based on the base station simulator technology, it can realize the monitoring of cell phone signal shielding, cell phone information collection and communication behavior in secret places. The system automatically collects mobile phones passing by or staying in secret-related places while it is turned on, and wirelessly shields personnel in the control area, blocking communication, and real-time monitoring of the status.

The mobile phone jammer is divided into 4 types
:- mobile, portable, conference room, and rack.
- Achieve real-time intelligent monitoring and control in order to effectively solve the information security problems brought about by mobile communication technology.

The proliferation of signal locator cell phone jammers and mobile phone communication jammers presents both challenges and opportunities in the realm of communication technology.
Signal locator cell phone jammers and mobile phone communication jammers operate on the principle of emitting interference signals that overpower the communication signals between mobile terminals and base stations. By employing white noise multi-band scanning and wide frequency spectrum coverage, these devices effectively disrupt communication channels, rendering mobile phones unable to connect to cellular networks.

Alongside the development of jammers, there's been a parallel advancement in mobile phone monitoring and intelligent management systems. These systems utilize mobile communication technology to detect MSIIMEI codes, control communication, and acquire mobile phone numbers within specific areas and environments. By employing base station simulator technology, these systems can monitor cell phone signal shielding, collect cell phone information, and monitor communication behavior in secretive locations.

Mobile phone jammers come in various types tailored to different needs
These include mobile jammers for individual use, portable jammers for on-the-go applications, conference room jammers for corporate settings, and rack-mounted jammers for centralized deployment. Each type serves specific purposes, from personal privacy protection to corporate information security.

- The proliferation of mobile communication technology has brought about information security challenges, including unauthorized data access, eavesdropping, and privacy breaches. Mobile phone jammers and monitoring systems play a role in addressing these challenges by preventing unauthorized communication and monitoring suspicious activities in sensitive environments.
- While mobile phone jammers and monitoring systems offer benefits in terms of security and privacy protection, their deployment and use may be subject to regulatory restrictions. It's essential to adhere to legal frameworks governing the use of such technologies to avoid legal consequences and ensure ethical practices.
- As technology evolves, finding the right balance between security measures and individual privacy rights becomes increasingly important. Organizations and individuals must weigh the benefits of employing mobile phone jammers and monitoring systems against potential privacy implications and ensure transparency and accountability in their implementation.
signal locator cell phone jammers and mobile phone communication jammers, alongside mobile phone monitoring and management systems, represent significant developments in addressing information security challenges in an increasingly connected world. However, their deployment requires careful consideration of regulatory compliance, ethical standards, and the balance between security and privacy.